Argus is a fixed-model Real Time Flow Monitor designed to track and report on the status and performance of all network transactions seen in a data network traffic stream. Argus provides a common data format for reporting flow metrics such as connectivity, capacity, demand, loss, delay, and jitter on a per transaction basis. The record format that Argus uses is flexible and extensible, supporting generic flow identifiers and metrics, as well as application/protocol specific information.
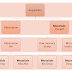
Argus is composed of an advanced comprehensive network flow data generator, the Argus sensor, which processes packets (either capture files or live packet data) and generates detailed network flow status reports of all the flows in the packet stream. Argus captures much of the packet dynamics and semantics of each flow, with a great deal of data reduction, so you can store, process, inspect and analyze large amounts of network data efficiently. Argus provides reachability, availability, connectivity, duration, rate, load, good-put, loss, jitter, retransmission, and delay metrics for all network flows, and captures most attributes that are available from the packet contents, such as L2 addresses, tunnel identifiers (MPLS, GRE, ESP, etc…), protocol ids, SAP’s, hop-count, options, L4 transport identification (RTP, RTCP detection), host flow control indications, etc.
Argus is used by many sites to generate network activity reports for every network transaction on their networks. The network audit data that Argus generates is great for security, operations and performance management. The data is used for network forensics, non-repudiation, network asset and service inventory, behavioral baselining of server and client relationships, detecting covert channels, and analyzing Zero day events.
Argus is an Open Source project, currently running on Mac OS X, Linux, Solaris, FreeBSD, OpenBSD, NetBSD, AIX, IRIX, Windows (under Cygwin) and OpenWrt, and has been ported to many hardware accelerated platforms, such as Bivio, Pluribus, Arista, and Tilera. The software should be portable to many other environments with littleor no modifications. Performance is such that auditing an entire enterprise’s Internet activity can be accomplished using modest computing resources.
Argus is composed of an advanced comprehensive network flow data generator, the Argus sensor, which processes packets (either capture files or live packet data) and generates detailed network flow status reports of all the flows in the packet stream. Argus captures much of the packet dynamics and semantics of each flow, with a great deal of data reduction, so you can store, process, inspect and analyze large amounts of network data efficiently. Argus provides reachability, availability, connectivity, duration, rate, load, good-put, loss, jitter, retransmission, and delay metrics for all network flows, and captures most attributes that are available from the packet contents, such as L2 addresses, tunnel identifiers (MPLS, GRE, ESP, etc…), protocol ids, SAP’s, hop-count, options, L4 transport identification (RTP, RTCP detection), host flow control indications, etc.
Argus is used by many sites to generate network activity reports for every network transaction on their networks. The network audit data that Argus generates is great for security, operations and performance management. The data is used for network forensics, non-repudiation, network asset and service inventory, behavioral baselining of server and client relationships, detecting covert channels, and analyzing Zero day events.
Argus is an Open Source project, currently running on Mac OS X, Linux, Solaris, FreeBSD, OpenBSD, NetBSD, AIX, IRIX, Windows (under Cygwin) and OpenWrt, and has been ported to many hardware accelerated platforms, such as Bivio, Pluribus, Arista, and Tilera. The software should be portable to many other environments with littleor no modifications. Performance is such that auditing an entire enterprise’s Internet activity can be accomplished using modest computing resources.